Introducing Valkyrie Verdict Plugins
One of the key benefits of Valkyrie Verdict is its ability to give a trusted verdict within 45 seconds on 92% of files (after automated analysis), and 4 hours on the remaining 8% (after human analysis). Our industry leading auto-analysis consists of several static and dynamic techniques, including state-of-the-art machine learning, precise detectors and dynamic behavior signatures.
Nevertheless, it is impossible to provide 100% threat visibility using automated techniques alone as many problems in malware analysis have been shown to be undecidable [1, 2]. Many of these results are based on the fact that precisely deciding whether a given program/input satisfies a certain post-condition, for an arbitrary post-condition, is undecidable. The proofs are based on two general techniques:
* Either they build a self-contradictory program assuming the existence of a decider for the given problem, similar to [3]
* They give a reduction from a well-known undecidable problem, such as the Halting Problem, similar to [4]
The 8% of unclassified files that require further testing are then analyzed by human experts who specialize in identifying complex and zero-day malware samples. Verdicts on these files are available to our users after 4-hours according to our SLA. Valkyrie customers can be confident that 100% of threats have been correctly identified after this 4 hour period. This isn’t some wild marketing claim - it is a scientific ‘100%’ built on the candid recognition that even the most advanced automatic tests available today cannot provide the correct verdict on all files. For those that remain, human analysis is absolutely essential. Users should always beware vendors that claim total protection based on automated mechanisms alone.
Customers who also use Comodo security solutions on their network are, of course, completely safe during this four-hour period. The 8% of unknown files will be isolated in a secure virtual container which cannot access other processes, system files or user data.
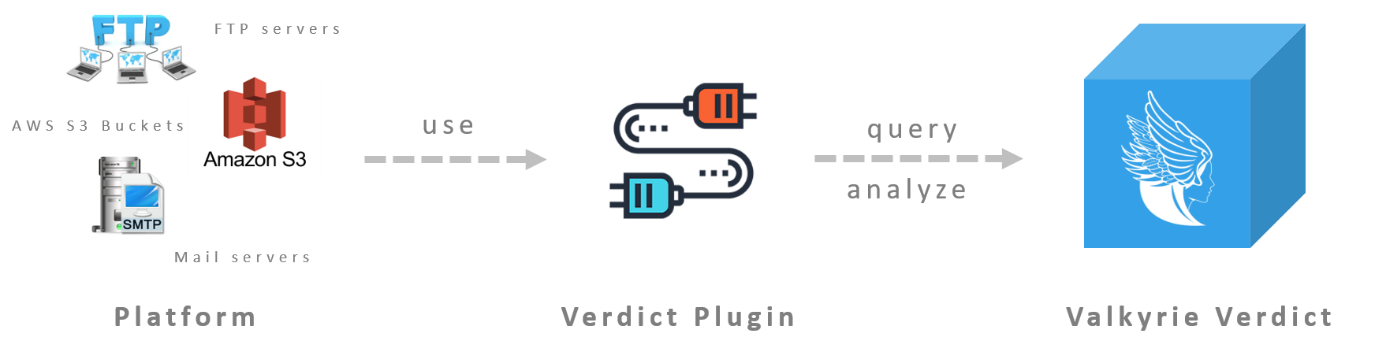
Figure 1 - https://developers.valkyrie.comodo.com/developers/plugins
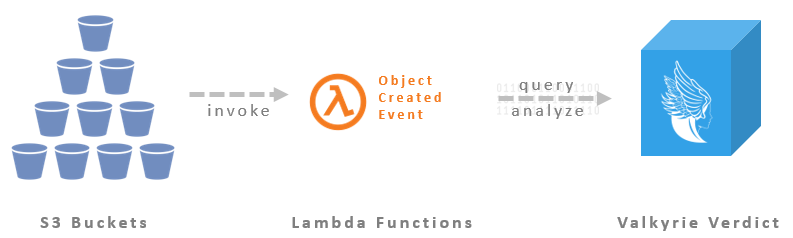
Threat Visibility on AWS S3 Buckets
What about the terabytes of data that is outside of your network – such as the files stored on Amazon S3 buckets? Amazon does not offer an out of the box file security solution that will ensure your files on the cloud are safe. Don’t worry, now you can use the AWS Lambda extension of Valkyrie Verdict to have 100% confidence that your S3 Bucket is safe from all threats. Verdict AWS S3 Background Watcher plugin monitors your buckets periodically and get verdict updates from Verdict backend. You should also integrate Verdict AWS S3 Background Watcher plugin and fully protect you buckets from zero-day malware threats.
For further information, just check out Verdict S3 Scanner Documentations:
- https://developers.valkyrie.comodo.com/developers/plugins/s3scanner
- https://developers.valkyrie.comodo.com/developers/plugins/s3periodicscanner
Protect Mail & FTP Servers
If you host a mail server, you most probably want to scan incoming attached files through emails and be sure that no malicious software is being distributed to your users / customers. Valkyrie Verdict has its Cross-Platform Command-Line Scanner (VVCLS) which you can easily integrate to your defense-in-depth for your mail servers. You can use VVCLS to scan each attachment and check scan output for any malware detection. VVCLS also supports Cloud based file analysis where you enable automatic upload of unknown files to Verdict backend and get %100 Visibility with %100 trusted file verdicts.
For further information, just check out Verdict Command-Line Scanner Documentation:

Valkyrie Verdict Linux Daemon Service
Verdict Daemon Service listens incoming connections under TCP socket and scans files or directories on demand. Daemon service supports similar commands with its command-line scanner alternative and reads several configuration values before starting the background service.
For further Information, just check out Valkyrie Verdict Linux Daemon Service Documentation:
[1] Ali A. Selçuk, Fatih Orhan, Berker Batur, "Undecidable Problems in Malware Analysis", 12th International Conference for Internet Technology and Secured Transactions (ICITST), 2017.
Online version: https://comodemia.comodo.com/Undecidable_Problems_in_Malware_Analysis.pdf
[2] David Evans, "On the Impossibility of Virus Detection", 2017.
Online version: https://enterprise.comodo.com/whitepaper/Impossibility_of_Virus_Detection_WP.pdf
[3] Fred Cohen, “Computer viruses: theory and experiments”, Computers and Security, 6(1):22-35, 1987
[4] Fred Cohen, “Computational aspects of computer viruses”, Computers and Security, 8(4):325-344, 1989.